Cryptography School Worksheets Results
Modular Arithmetic and Cryptography! - University of California, Irvine
of cryptography. We call the act of testing all 25 options until nding the key, the method of brute force. However, even if we couldn’t use brute force the Caesar cipher is still considered to be weak. This is because each letter of the alphabet (say \a") always gets encrypted to the same letter (which depends on your shift).
https://url.theworksheets.com/464i421 Downloads
Preview and Download !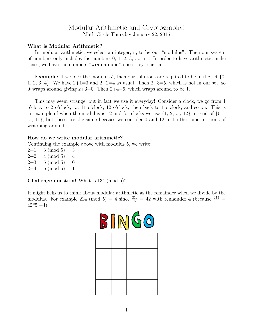


CIPHER WORKSHEETS - Escape Lincoln
CIPHER WORKSHEETS CAESAR CIPHER In cryptography, a Caesar cipher, also known as a Caesar shift cipher or shift cipher, is one of the simplest and most widely-known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions further down the alphabet.
https://url.theworksheets.com/2mq5202 Downloads
Preview and Download !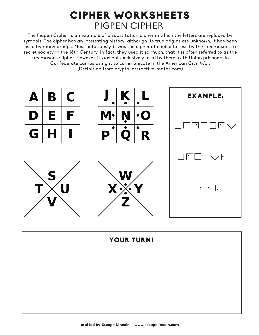
Cryptography Worksheet The Atbash Cipher - Crypto Corner
Cryptography Worksheet — The Atbash Cipher Gsv Zgyzhs Xrksvi The Atbash Cipher is a very old Subs tu on Cipher that was originally developed for use with the Hebrew alphabet. In fact, in the Book of Jeremiah there are several words that have been enciphered using the Atbash Cipher.
https://url.theworksheets.com/7s6d76 Downloads
Preview and Download !


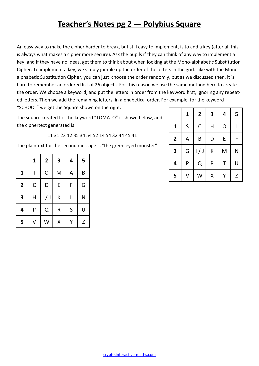
Cryptography Worksheet Polybius Square - Crypto Corner
Cryptography Worksheet — Polybius Square Long Encryp on Choose a keyword. Choose a paragraph to encrypt from a book. Encrypt the passage using a Polybius Square with you chosen keyword. Pass the encrypted passage to someone else in the class for them to decrypt. DO NOT give them the keyword.
https://url.theworksheets.com/7tfs59 Downloads
Preview and Download !

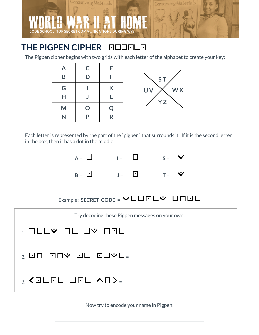
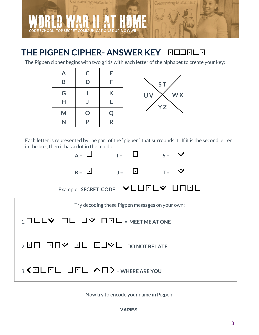
Cryptography Worksheet The - Crypto Corner
Cryptography Worksheet — The Pigpen Cipher The Pigpen Cipher is a Subs tu on Cipher that was used by the Freemasons in the 18th Century. They subs tuted each le ©er of the alphabet with a picture. Using the diagram on the le L, can you decipher the two mathema cal words below?
https://url.theworksheets.com/6gs9128 Downloads
Preview and Download !


The mathematics of cryptology - UMass
cryptography is based on the following empirically observed fact (here written as if it were carved in stone): Multiplying two integers is easy, but finding a nontrivial factor of an integer is hard. In other words, integer multiplication is in practice a “one-way function.” If a number is large, it’s essentially impossible to factor it. 11
https://url.theworksheets.com/340l71 Downloads
Preview and Download !


Cryptography: An Introduction (3rd Edition) - UMD
cryptography and one deals with formal approaches to protocol design. Both of these chapters can be read without having met complexity theory or formal methods before. Much of the approach of the book in relation to public key algorithms is reductionist in nature.
https://url.theworksheets.com/31n1212 Downloads
Preview and Download !


CODE SCHOOL: TOP SECRET COMMUNICATIONS DURING WWII - The National WWII ...
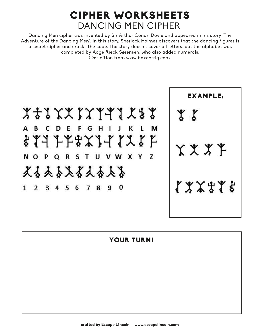
CODE SCHOOL: TOP SECRET COMMUNICATIONS DURING WWII Codes and Ciphers A code is a word or message that is replaced with an agreed code word or symbol. A cipher is when each letter in an alphabet is replaced with another letter, number, picture, or other symbol. Ciphers always have key that is shared among those sending and receiving the message ...
https://url.theworksheets.com/7lp656 Downloads
Preview and Download !
Unplugged - Houston Independent School District
Unplugged Activities E lem e n ta r y D es cri p tio n Kodable https://hourofcode.com/kodable-pre K-5 Lesson Plans My Robotic Friend https://curriculum.code.org/csf ...
https://url.theworksheets.com/7tfx77 Downloads
Preview and Download !


Cryptography Worksheet The Atbash Cipher - Crypto Corner
Cryptography Worksheet — The Atbash Cipher Gsv Zgyzhs Xrksvi The Atbash Cipher is a very old Subs tu on Cipher that was originally developed for use with the Hebrew alphabet. In fact, in the Book of Jeremiah there are several words that have been enciphered using the Atbash Cipher.
https://url.theworksheets.com/7tfz71 Downloads
Preview and Download !


<< Previous results Next results >>