Cryptography School Worksheets Results
A beginner's guide to codebreaking 1 - National Cipher Challenge 2022
School of Mathematical Sciences University of Southampton Version 1.2 29th September 2019 Graham A. Niblo On ciphers version 1.2, Page 1. ... At the cutting edge of cryptography it is the interaction of those disciplines with mathematics which enables governments (and criminal hackers)
https://url.theworksheets.com/7tg159 Downloads
Preview and Download !


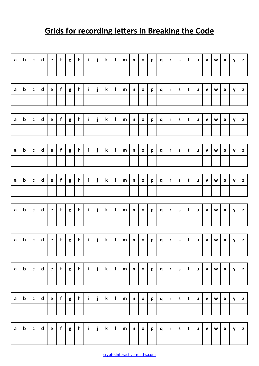
Cryptography Worksheet Breaking the Code - Crypto Corner
Cryptography Worksheet — Breaking the Code You have been given this encrypted message, and all you know is that it has been encrypted using a ... Worksheets Author: Dan Created Date: 20130105212054Z ...
https://url.theworksheets.com/4yli163 Downloads
Preview and Download !

math made fun! - SharpSchool
About This Book Math Made Fun! is designed to give students lots of solid practice in developing their computation skills. Problems are presented in a fun and engaging format that is appealing
https://url.theworksheets.com/73c469 Downloads
Preview and Download !

Cryptography Worksheet Transposi on Ciphers 1
cryptography. It was used by the Ancient Greeks, and specifically the Spartans, to send secret messages during military campaigns. Both the sender and receiver would need iden cal rods (the same length and diameter). The sender of the message would wrap a long thin piece of
https://url.theworksheets.com/6grs134 Downloads
Preview and Download !


Th e Mathematics of Encryption - American Mathematical Society
Cryptography is one of the oldest studies, and one of the most active and important. The word cryptography comes from two Greek words: κρυτττ`oςς (kryptos), meaning secret, and γραϕω` (grapho), meaning to write. As theserootsimply, it allbegan withtheneedforpeopletocom-municatesecurely. The basicsetupis that there aretwo people ...
https://url.theworksheets.com/7tg383 Downloads
Preview and Download !


Lesson Plan > CYBERSECURITY - CompTIA’s Future of Tech
• Invite guest speakers from the field to your class to discuss the role that cybersecurity plays in business, school and/or public service. • Search the Internet for age-appropriate activities related to the keywords cryptography, computer forensics and hacking to extend learning opportunities for your students. //
https://url.theworksheets.com/7cds42 Downloads
Preview and Download !


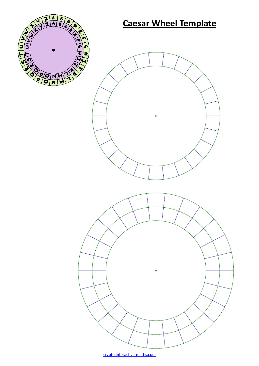
Cryptography Worksheet The Caesar Shi - Crypto Corner
Cryptography Worksheet — The Caesar Shi Julius Caesar used a simple Subs tu on Cipher to send messages to his troops. He used a very simple rule to replace each le ©er with another le ©er from the alphabet. He subs tuted each le ©er by the le ©er
https://url.theworksheets.com/4ylq91 Downloads
Preview and Download !

Number Theory Applications in Cryptography - Montclair State University
curves were explored on a smaller scale as they are also applied in cryptography. For a fixed prime number . p. and a special class of elliptic curves over Zp, we investigate how many of them intercept the y-axis. Additionally, the research presented in this paper was successfully implemented into a middle school classroom.
https://url.theworksheets.com/7tg846 Downloads
Preview and Download !


Cryptography Lesson Plan
Introduction Cryptography.pdf5 Worksheet – The Caesar Cipher 10 CryptographyWorksheets.pdf Class Discussion - Breaking Encryption 5 Cryptography.pdf Party explanation 5 Cryptography.pdf Encode surprise party 10 CryptographyWorksheets.pdf Decode surprise party Cryptography10 Worksheets.pdf Wrap-up Discussion 5 Cryptography.pdf
https://url.theworksheets.com/6grx144 Downloads
Preview and Download !


<< Previous results